A few thoughts on Cryptography Engineering
Submitted by: Suvankar Roy Goswami
(Department of BCA, BAtch :2017-2020)
University Roll Number : 15201219093
Cryptography
Cryptography is a method of protecting information and communications through the use of codes so that only those for whom the information is intended can read and process it. The pre-fix “crypt” means “hidden” or “vault” and the suffix “graphy” stands for “writing”.

In computer science, cryptography refers to secure information and communication techniques derived from mathematical concepts and a set of rule-based calculations called algorithms to transform massages in ways that are hard to decipher. These deterministic algorithms are used for cryptographic key generation and digital signing and verification to protect data privacy, web browsing on the internet and confidential communication such as credit card transactions and email.
Application of cryptography
Government and Military:
The oldest application of cryptography is the protection of military secrets. One of the oldest known ciphers in he Caesar Cipher, attribute to Julius Caesar and was used to send confidential information to his commanders and soldiers in the field. Since then, the use of cryptography in government and the military has only increase to protect information that is sensitive for reasons of tactics, politics etc.
The Internet :
A massive use of cryptography in the modern world is on the internet. The Hyper Text Transfer Protocol Secure (HTTPS) is the method by which sensitive information is communicate to and from the internet. Each time a website with a “green lock” icon is visited, modern cryptography ciphers are in use to protect the information flowing between the site and the visiting computer.
Password Security:
Many people use password to handle their collection of passwords for different sites. These passwords are stored in an encrypted format to protect them against attackers.The password manager takes a master password and uses it to decrypt the other stored password.
Secure Email:
The general email standard is defined to transmit text data from place to place, so all email is sent unencrypted. Web-based email (Gmail, Yahoo etc) use HTTPS to encrypt email, but it is also possible to encrypt other email with tools like PGP(Pretty Good Privacy) so that only the sender and recipient have access.
Business Data:
Most business have information that they wish remains secret: intellectual property, customer data etc. In some cases, it is required by law to encrypt sensitive information about customers about customers and any breach of data must be disclosed to the public.
History of cryptography
Before modern era, cryptography focused on message confidentiality conversion of messages from a comprehensible from into an incomprehensible one and back again at the other end, rendering it unreadable by interceptors or eavesdroppers without secret knowledge (namely the key needed for decryption of that messages) . Encryption attempted to ensure secrecy in communications , such as those spies, military and diplomats.

Reconstructed ancient Greek scytale, an early cipher device
 |
|
Cryptography techniques
Cryptography is closely related to the disciplines of cryptography and cryptanalysis includes techniques such as microdots, merging words with images, and other ways to hide information in storage or transit. However, in today’s computer-centric world, cryptography is most offen associated with scrambling plaintext (ordinary text, sometimes referred to as cleartext) into ciphertext (a process called encryption) then back again (known as decryption). Individuals who practice this field are known as cryptographers.
Modern cryptography concerns itself with the following four objects:
- Confidentiality: The information cannot be understood by anyone for whom it was unintended.
- Integrity: The information cannot be altered in storage or transit between sender and intended receiver without the alternation being detected.
- Non-reputation: The creator/sender of the information cannot deny at a later stage his or her intentions in the creation or transmission of the information.
- Authentication: The sender and receiver can confirm each other’s identity and the origin/destination of the information.
Procedures and protocols that meet some or all of the above criteria are known as cryptosystems. Cryptosystems are often thought to refer only to mathematical procedures and computer programs; however they also include the regulation of human behaviour, such as choosing hard-to-guess password , logging off unused systems and not discussing sensitive procedures with outsiders.
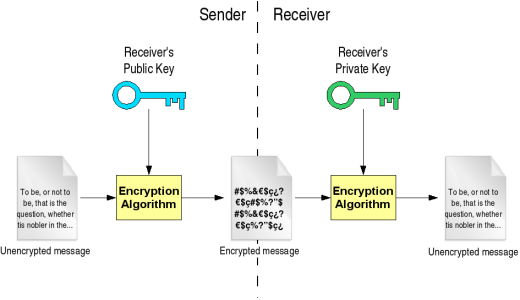
Cryptographic algorithms
Cryptosystems use a set of procedures known as cryptographic algorithms, or ciphers, to encrypt and decrypt messages to secure communications among computer systems, devices such as smartphones, and applications. A cipher suite uses one algorithm for encryption, another algorithm for message authentication and another for key exchange. This process, embedded in protocols and written in software that runs on operating systems and network computer systems, involves public and private key generation for data encryption/decryption, digital signing and verification for message authentication, and key exchange.
Types of cryptography algorithms
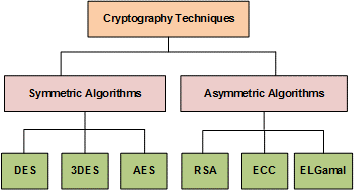
There are two types of cryptography algorithms:
- Symmetric algorithm:
Symmetric algorithms are sometimes referred to as secret key algorithms. This is because these types of algorithms generally use one key that is kept secret by the systems engaged in the encryption and decryption process. This single key is used for both encryption and decryption.
Symmetric key algorithm tend to be very secure. In general, they are considered more secure that asymmetric key algorithms. There are some symmetric key algorithms are considered virtually unbreakable. Symmetric key algorithm are also very fast. This is why they are often used in situations where is a lot of data that needs to be encrypted.
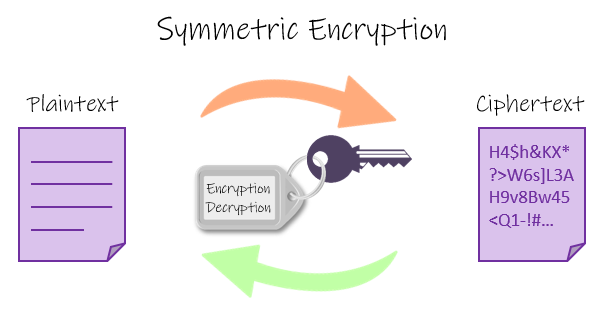
In symmetric key algorithms, the key is shared between the two systems. This can present a problem. You have to figure out way to get the key to all systems that will have encrypt or decrypt data using symmetric key algorithm. Having to manually distribute a key to all systems can be quite cumbersome task. Sometimes, this can only be done by copying the key from a central location. You can imagine how troublesome that can be. On windows system, , you do have the option of possibly using a group policy or a script of some kind to copy the key to the necessary systems. This helps, but the administrator is still responsible for making sure the group policy or the script function properly.
There are hundreds of different Symmetric key algorithms available. Each has its own strengths and weaknesses. Some of the more common examples are DES, 3DES, AES, IDEA, RC4 and RC5.
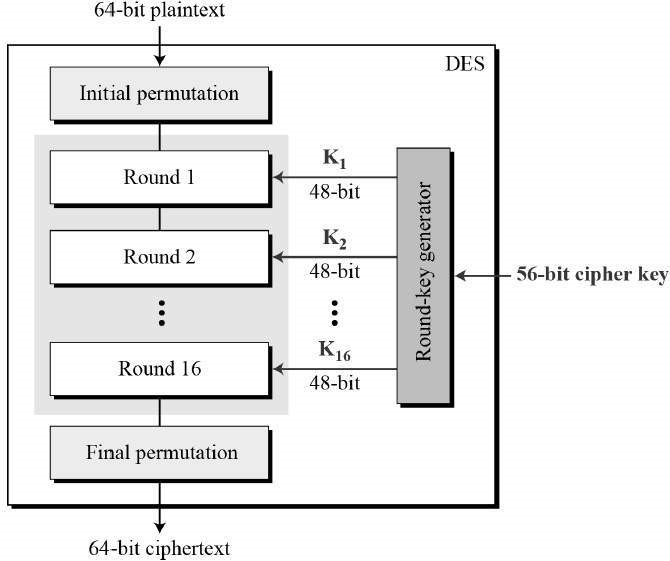
DES: It is the Data Encryption Standard. DES was originally Developed in 1976. It has been one of the most widely used encryption algorithms. This is partially due to the fact that it was adopted as the government standard for encryption. The DES algorithm itself is very strong. The weakness comes in the fact that the original DES standard uses a 56-bit encryption key. Basically, you can use a computer to run through all bit combinations of the key(1s and 0s) until you hit the right key. Back when DES was originally developed, this would have taken hundreds of years. Nowadays, it might only take a day or so to run through all the combinations. This is the main reason why DES is no longer used.
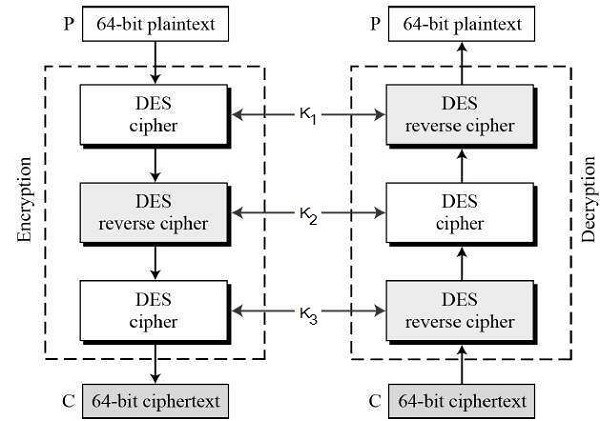
3DES: It is mostly commonly known as Triple DES. 3DES gets its name because it applies the DES algorithm three times to each block of data. 3DES has overtaken its predecessor, DES and is currently considered to the most widely used standard for secure encryption. The algorithm itself is just as strong as DES, but you also have the advantage of being able of the 3DES encryption iterations. The most secure implementation is use a different key for each iteration, if you use the same key for all three iterations, the key strength is considered to be 56 bits. That’s basically the same as DES. If you use the same key for two of the iterations and a different key for the third, then the key strength is considered to be 112 bits. If you use a different key for all three iterations, then the encryption strength is considered to 168 bits. For a long time, the 3DES algorithm was the main algorithm used in FIPS 140 complaint windows implementations. When you configured the windows group policy or the registry that forced the use of FIPS 140 compliant algorithms, you were basically forcing the use of 3DES for encryption. Now windows systems offer the use of AES, which is also a FIPS 140 compliant algorithm.
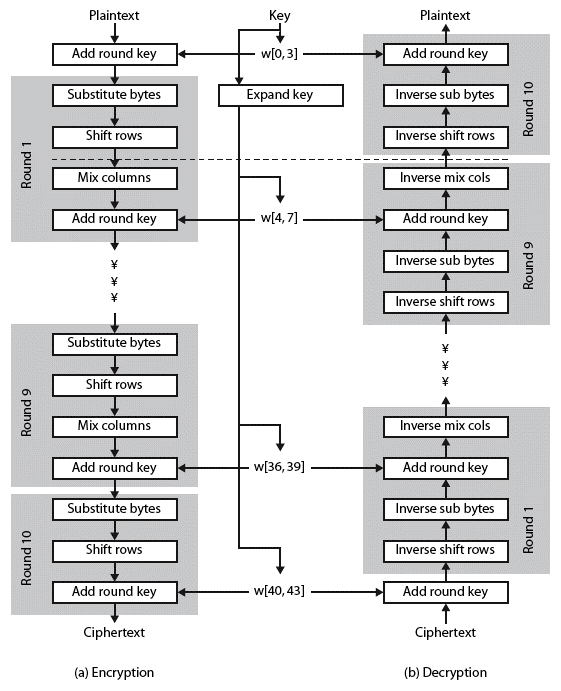
AES: it is Advanced Encryption Standard. It is also sometimes referred to as an Rijndael algorithm. This is due to the fact that AES actually comes from the Rijndael algorithm. The government had an evaluation process to determine which algorithm would be used as the AES standard, and the Rijndael algorithm was chosen as the winner. The AES standard actually includes three different ciphers: AES-128, AES-192, and AES-256. The numbers represent the length of the encryption key. AES is very fast and very secure. Because of this, its global uptake has been very quick.
IDEA: It is the International Data Encryption Algorithm. IDEA was originally meant to be a replacement for the DES standard. IDEA uses a 128-bit encryption key. There are two main reasons IDEA is not as widely used as planned. The first is the fact that IDEA is subject to a range of weak keys. The second reason is that there are currently faster algorithms that produce the same level of security.
- Asymmetric algorithm:
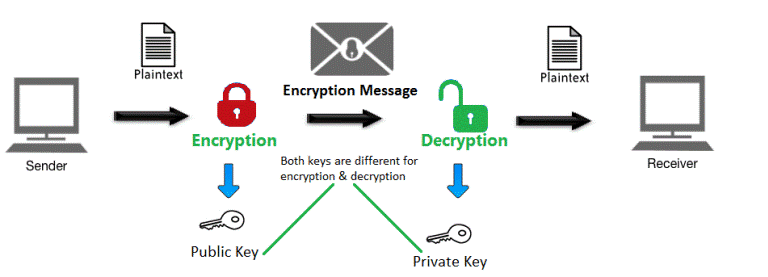
Asymmetric cryptography also known as public key cryptography. Uses public and private keys to encrypt data. The keys are simply large numbers that have been paired together but are not identical. One key in the pair is kept secret; it is called the private key. Either of the keys can be used to encrypt a message; the opposite key from the one used to encrypt the message is used for decryption.
Many protocols like SSH, OpenPGP, S/MIME and SSL/TLS rely one asymmetric cryptography for encryption and digital signature functions. It is also used in software programs, such as browsers, which need to establish a secure connection over an insecure network lite internet or need to validate a digital signature. Encryption strength is directly tied to key size and doubling the key length delivers an exponential increase in strength, although it does impair performance. As computing power increases and more efficient factoring algorithms are discovered, the ability to factor large and large numbers also increases.
For asymmetric encryption to deliver confidentiality, integrity, authenticity and non-reputability, users and systems need to be certain that key is authentic, that it belongs to the person or entity claimed and that it has not been tampered with nor replace by malicious third party. There is no perfect solution to this public key authentication problems. A public key infrastructure (PKI) -where trusted certificate authorities certify ownership of key pairs and certificates – is the most common approach, but encryption products based on the Pretty Good Privacy(PGP) model – including OpenPGP—rely on a decentralized authentication model called a web of trust, which relies on individual endorsements of the link between user and public key.
There are hundreds of different Asymmetric key algorithms available. Each has its own strengths and weaknesses. Some of the more common examples are RSA, ECC, ELGamal etc.
RSA: Rivest-Shamir-Adleman – the most widely used asymmetric algorithm – is embedded in the SSL/TSL protocols which is used to provide communications security over a computer network. RSA derives its security from the computational difficulty of factoring large integers that are the product of two large prime numbers.
 |
Multiplying two large primes is easy, but the difficulty of determining the original numbers from the product – factoring – forms the basis of public key cryptography security. The time it takes to factor the product of two sufficiently large primes is considered to be beyond the capabilities of most attackers, excluding nation-state actors who may have access to sufficient computing power. RSA keys are typically 1024 or 2048-bits long, but experts believe that 1024-bits keys could be broken in the near future, which is why government an industry are moving to a minimum key length 2048-bits.
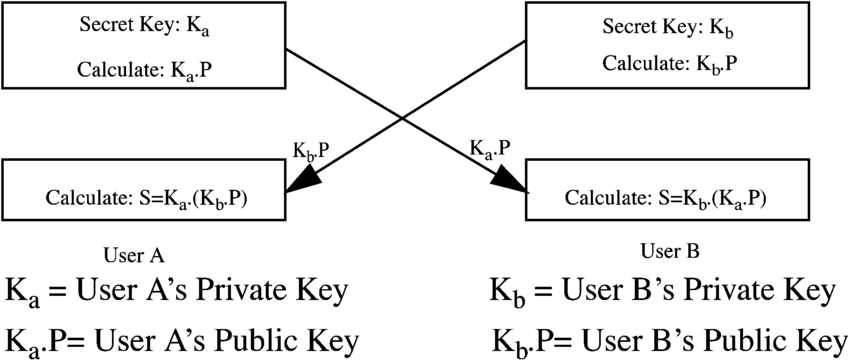
ECC: Elliptic Curve Cryptography (ECC) is gaining favour with many security experts as an alternative to RSA for implementing public key cryptography. ECC is a public key encryption technique based on elliptic curve theory that can create faster, smaller and more efficient cryptography keys, ECC generates keys through the properties of the elliptic curve equation.
To break ECC, one must compute an elliptic curve discrete logarithm, and it turns out that this is a significantly more difficult problem that factoring. As a result ECC key sizes can be significantly smaller than those required by RSA yet deliver equivalent security with lower computing power and battery resources usage making it more suitable for more applications than RSA.
|
A block diagram of ECC secret key algorithm |
RSA vs. ECC
- RSA Advantages:
- Has been around longer; math well-understood
- Patent expired; royalty free
- Faster encryption
- ECC Advantages:
- Shorter key size
- Fast key generation (no primality testing)
- Faster decryption
How asymmetric encryption works
Asymmetric encryption algorithm use a mathematically-related key pair for encryption and decryption; one is the public key and other is the private key. If the public key use for encryption , the related private key is use for decryption.
Only the user or computer that generated the key pair has the private key. The public key can be distributed to anyone who wants to send encrypted data to the holder of the private key with the public one.
Two participants in the asymmetric encryption workflow are the sender and the receiver. First the sender obtains the receiver’s public key. Then the plaintext is encrypted with the asymmetric encryption algorithm using the recipient’s public key, creating the chipertext. The chipertext is hen sent to receiver, who decrypts the chipertext with his private key so he can access the sender’s plaintext.
Because of the one-way nature of the encryption function, one sender is unable to read the messages of another sender, even though each has the public key of the receiver.
Uses of asymmetric cryptography
The typical application for asymmetric cryptography is authenticating data through the use of digital signature. Based on asymmetric cryptography, digital signature can provide assurances of evidence to the origin, identity and status of an electronic document, transaction or massage, as well as acknowledging informed consent by the signer.
To create a digital signature, signing software – such as an email program—creates a one-way hash of the electronic data to be signed. The user’s private key is then used to encrypt the hash, returning a value that is unique to the hashed data. The encrypted hash, along with other information such as the hashing algorithm, forms the digital signature. Any change in the data, even to a single bit, results in the different hash value.
This attribute enables others to validate the integrity of the data by using the signer’s public key to decrypt the hash. If the decrypted hash matches a second computed hash of the same data. It proves that the data hasn’t change since it was signed. If the two hashes don’t match, the data has either been tampered with in some way – indicating a failure of integrity – or the signature was created with a private key that doesn’t correspond to the public key presented by the signer indicating failure of authentication.
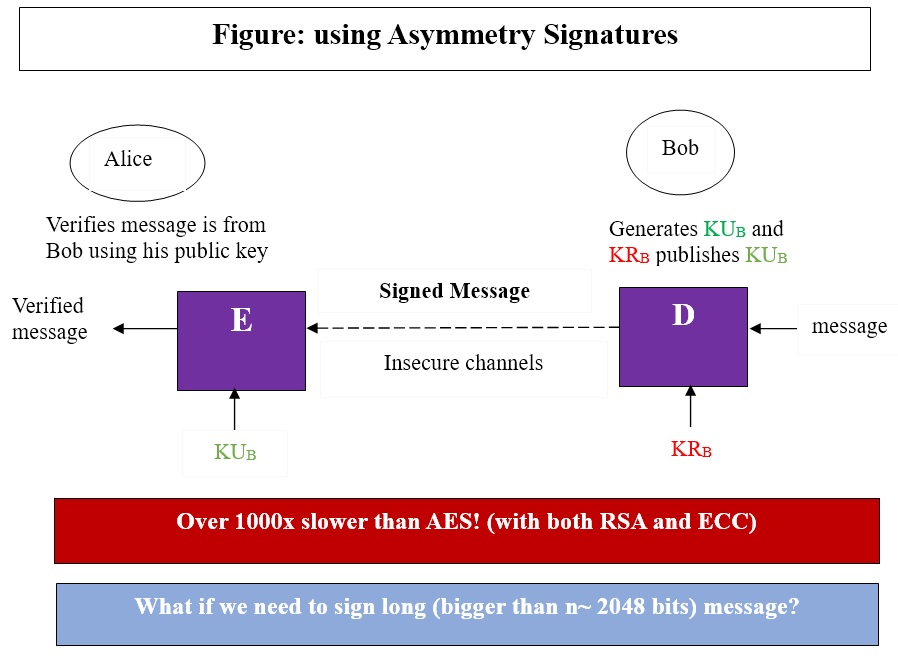
|
A block diagram of ECC secret key algorithm |
A digital signature also makes it difficult for the signing party to deny having signed something – the property of non-repudiation. If a signing party denies a valid digital signature, their private key has either been compromised or they are being signatures have the same legal weight as more traditional forms of signatures.
Asymmetric cryptography can be applied to systems in which many users may need to encrypt messages, such as encrypted email, in which public key can be used to encrypt a message and private key can be used to decrypt it.
The SSL/TSL cryptographic protocols for establishing encrypted links between websites and browsers also make use of asymmetric encryption.
Additionally Bitcoin and other cryptocurrencies rely on asymmetric cryptography as users have public keys that every one can see and private keys that are kept secret. Bitcoin uses a cryptographic algorithm to ensure that only the legitimate owners can spend the funds.
In the case of the Bitcoin ledger, each unspent transaction output(UTXO) is typically associated with a public key. So if the user X, who has an UTXO associated with his public key, want to send money to user Y, user X uses his private key to sign a transaction that spends the UTXO and creates a new UTXO that’s associated with user Y’s public key.
Symmetric vs. Asymmetric key Cryptography
- Symmetric-Crypto (DES, 3DES, AES)
- Efficient (smaller keys / faster encryption) because of simpler operations (e.g. discrete log)
- Key agreement problems
- Online
- Asymmetric-Crypto (RSA, ECC)
- RSA 1000x slower than DES, more complicated operations (e.g. modular exponentiation)
- How to publish public key? Requires PKI / Cas
- Offline or online
