A Brief Introduction to Cryptography and Encryption Algorithms
Submitted By : Alapan Ghosh (Department of BCA, Batch:2016-2019)
In this world of fast moving technology, security of information is more important than it has ever been before. There are various ways to achieve that, and a prominent role in this frontier is played by Cryptography. It is used in almost every domain of Information Technology, including but not limited to network access points(routers, switches, physical firewalls,etc), messaging apps, banking systems and even in voice communication.
But what is Cryptography?
Cryptography in simple words is the art of encoding (Encryption) and decoding(Decryption) of messages. Messages are encrypted before they are sent so that no intruder in the network can intercept them, and later need to be decrypted so that the recipient can understand the message(s).
The most simple form of cryptography is Symmetric Key Encryption. The messages are encrypted using a 'key' which is later used to decrypt the message. Imagine it like a door. You use a key to lock it and you would need the same key to unlock it. The diagram below shows how it works.
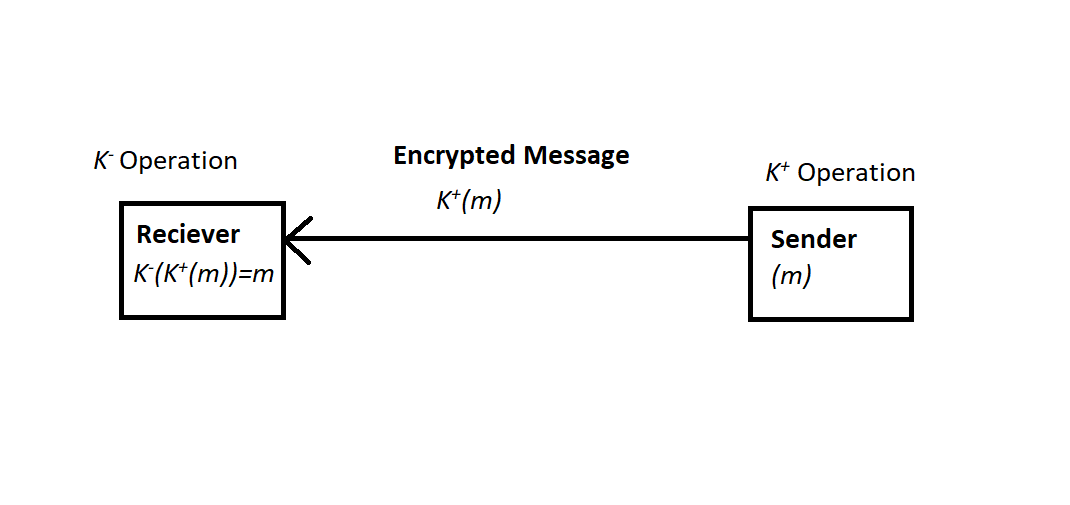
In the figure above, the Sender sends a message, lets say m, and the encryption is performed on it(K+ operation) using the key K. The encrypted message K+(m) is sent over to the Receiver. Now even if someone reads the whole message that is being transferred, they wont be able to understand it because it is encrypted. When the Receiver gets the message, they perform decryption of the received message(K- Operation) using the same key K, and get back the original message m.
There are many different Symmetric Key Encryption algorithms and some of them are CipherText Auto Key(CTAK), Twofish , Data Encryption Standard(DES), Triple DES, Advanced Encryption Standard(AES),etc.
But with Symmetric Key algorithms, there is one small problem. For the both parties to communicate, they need to agree on a common key K, which they need to share with each other publicly. The key itself can get intercepted by an intruder and compromise the whole communication. There are many ways to combat this issue. One of them is the Diffie-Hellman Key Exchange algorithm, with which the two(or more) parties can publicly exchange keys without actually revealing the key. But even this has drawbacks. A better alternative is to use Asymmetric Key Encryption.
Asymmetric Key Encryption or Public Key Encryption doesn't use a common key K for both encryption and decryption but uses two mathematically related keys. The receiver generates two mathematically related keys called Private Key and Public Key, where the Private Key is kept safe, and the Public Key is shared with the sender. The sender then encrypts messages using the Public Key and sends it to the receiver, where it is decrypted using the Private Key to get the original message. Even if an intruder knows the Public Key(which is openly shared anyway), he/she cant decrypt the message because it requires the Private Key.
You can imagine it like a mailbox. Anyone who knows your address(Public Key) can go to your mailbox and drop a message. But only you who has the key to the mailbox(Private Key) can open the mailbox and read the messages. The figure below shows how it works.
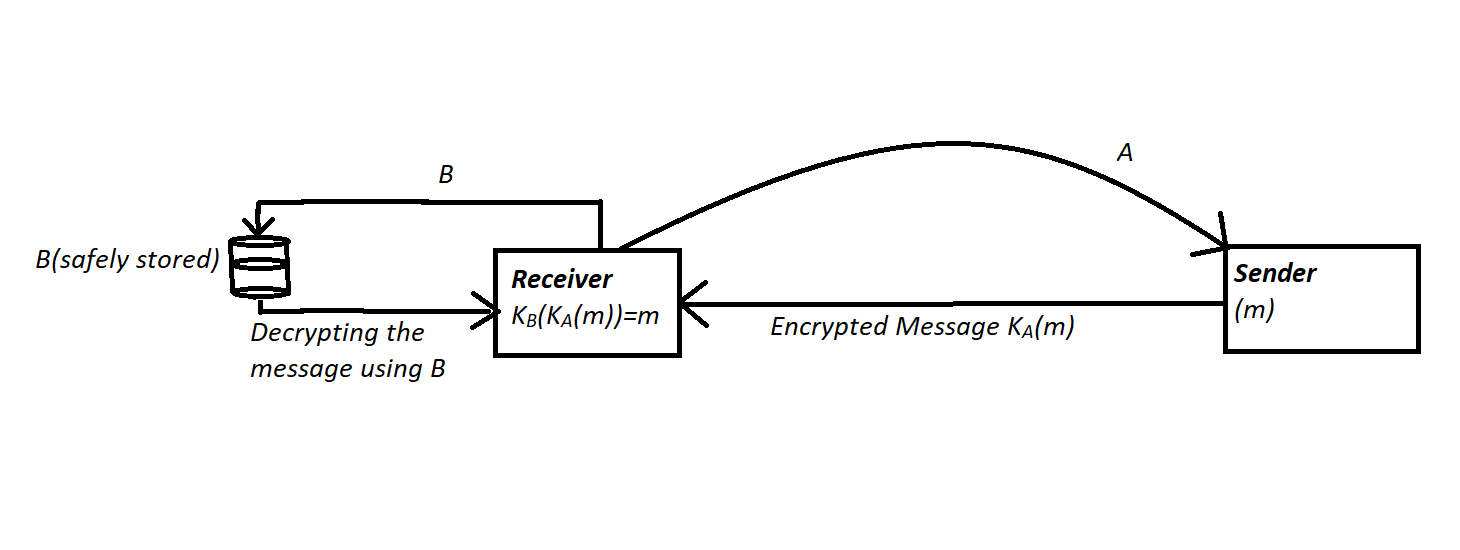
In the figure above, the process begins with the Receiver generating two keys A and B. A is shared with the Sender as the Public Key whereas B is stored safely as the Private Key. The Sender uses A to encrypt the message m and sends the encrypted message KA(m) to the Receiver. The Receiver now uses the Private Key B to decrypt the received message and get the backs the original message m. It should be noted that for some cryptosystems, whether A is the Public Key and B is the Private key, or vice versa doesn't matter. They would work both ways, i.e.
KB(KA(m)) = m = KA(KB(m))
Different examples of Public Key Encryption algorithms are RSA, ElGamal Cryptosystem, Elliptic Curve Cryptography, etc. It is one of the most secure cryptography method and is widely used in the field of IT. SSL(Secure Socket Layer), SSH(Secure Shell), HTTPS(Secure HTTP) and even cryptocurrencies like Bitcoin and Ethereum uses Asymmetric Key Encryption. Recently, WhatsApp is using a feature called End-to-end Encryption which is another example of the same.
Even though these algorithms are quite effective, they require substantial amount of processing power which makes it unsuitable for lightweight systems like sensors in a sensory network, drones,etc. In such cases, a variety of non standard algorithms and protocols are used such TESLA, μTESLA, SPINS,etc.
